Password strength is a measure of the effectiveness of a password in resisting guessing and brute-force attacks. In its usual form, it estimates how many trials an attacker who does not have direct access to the password would need, on average, to guess it correctly. The strength of a password is a function of length, complexity, and unpredictability
Websites have a responsibility to users to accurately tell them how good a password is, and this is not an easy job.
- If your password is 8 characters long and only formed of lower case characters, you need to make it better, perhaps by adding a number or more characters.
- If your password is 25 characters long but happens to not contain a number, you shouldn't be forced by a password security policy to add one, you clearly have a very secure password.
Complexify aims to provide a good measure of password complexity for websites to use both for giving hints to users in the form of strength bars, and for casually enforcing a minimum complexity for security reasons.
Using strong passwords lowers overall risk of a security breach, but strong passwords do not replace the need for other effective security controls. The effectiveness of a password of a given strength is strongly determined by the design and implementation of the authentication system software, particularly how frequently password guesses can be tested by an attacker and how securely information on user passwords is stored and transmitted. Risks are also posed by several means of breaching computer security which are unrelated to password strength. Such means include wiretapping, phishing, keystroke logging, social engineering, dumpster diving, side-channel attacks, and software vulnerabilities.
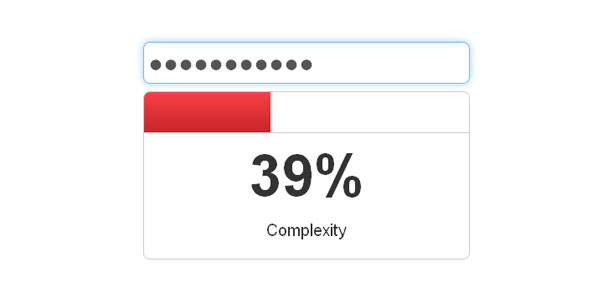
Complexity Rating
Complexify's default settings will enforce a minimum level of complexity that would mean brute-forcing should take ~600 years on a commodity desktop machine. The 'perfect' password used to scale the complexity percentage would take 3x10^33 years. These are equivalent to a 12 character password with uppercase, lowercase and numbers included, and a 25 character password with uppercase, lowercase, numbers and a wide range of punctuation.
Unicode
Complexify supports Unicode and will add appropriate complexity for the size of character set included in a password.
For example, as there are 96 Hiragana characters defined in the Unicode specification, including one of these will increase the brute-force complexity by 96.
The rationale behind this is that in an attacker were wanting to include Japanese passwords in his attack, he/she may choose to include the Hiragana set in his/her attack, but not the Katakana set. Complexify divides Unicode into 94 appropriately grouped sets.
How to use Complexify?
Complexify is a jQuery plugin, so you will already need to have jQuery included on your page. Other than this, just include the file in your
like this:<script type="text/javascript" src="/js/jquery.complexify.js"></script>...and then apply it to a password field like this:
$("#password").complexify(options, callback(valid, complexity){...}); The valid argument passed to your callback function is a boolean that indicates whether the password met the minimum number of password characters and the minimum level of complexity. The complexity argument is a percentage where 100% represents a 'perfect' password of 25 characters containing one element from each available character set.
What Complexify doesn't do:
- It does not take into account possible dictionary attacking of passwords. However most passwords vulnerable to this method are relatively short and contain only letters, making them score fairly weakly on this test anyway.
- It's still just client-side validation. If someone wants to bypass this they can, I recommend implementing a check for the minimum length on the server, but I am considering making a complementary server-side library that will enable developers to have a consistent policy set up throughout their service.







As your article mentions “strong passwords do not replace the need for other effective security controls”. And in my opinion some form a 2FA is a must to maintain effective security. Always having a complicated password (That you can remember) for every different online account is not possible. However one of the first things I look for when setting up any account is if they offer 2FA (two-factor authentication) where I can telesign into my account. I also have contacted some of the organizations to see if they plan on providing 2FA. When I have this, it gives me the confidence that my account won’t get hacked and my personal information isn’t vulnerable.
As for me, I dislike signing e.g. with mobile phone, but in real world it’s necessary. Of course, not every website has possibility to implement such type of auth (mobile, usb tokens etc)